Cybersecurity Risk Management Best Practices B78

Cybersecurity Risk Management Best Practices B78 Cybersecurity risk management in cybersecurity risk management: mastering the fundamentals using the nist cybersecurity framework, veteran technology analyst cynthia brumfield, with contributions from cybersecurity expert brian haugli, delivers a straightforward and up to date exploration of the fundamentals of cybersecurity risk planning and management. the book offers readers easy to. Cybersecurity council 15, 27 cybersecurity risk management and best practices (csric iv wg4 final report) 111 damage assessment 90 limitation see limitation reputational 11, 38, 92 bindex.indd 133 29 11 2021 09:35:52.
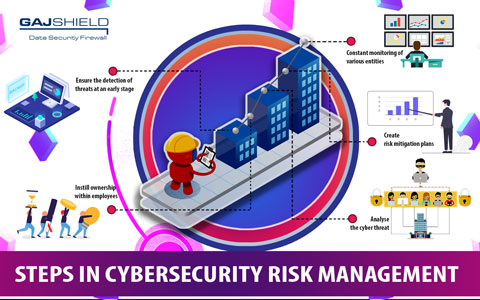
Cybersecurity Risk Management Best Practices B78 Cybersecurity risk management “best practices” are flexible and scalable for companies of all sizes. as such, the smb feeder group’s objectives are as follows: explain, in basic terms, why cybersecurity is important and what smbs can achieve by using the wg 4 document to improve their cybersecurity risk management practices. It fosters communication among both internal and external stakeholders about cybersecurity, and for larger organizations, helps to better integrate and align cybersecurity risk management with broader enterprise risk management processes as described in the nistir 82865 series. the framework is organized by five key functions– identify. Business objectives. focusing on the use of risk registers to set out cybersecurity risk, this document explains the value of rolling up measures of risk usually addressed at lower system and organization levels to the broader enterprise level. keywords cybersecurity risk management (csrm); cybersecurity risk measurement; cybersecurity risk. Cisa cyber essentials chapter 1: yourself, the leader video. this half hour video provides a deep dive into toolkit 1 which focuses on you as a leader and how your investment (e.g., time and money) drives actions and activities, and these build and sustain a culture of cybersecurity within your organization.

Cybersecurity Risk Management Best Practices B78 Business objectives. focusing on the use of risk registers to set out cybersecurity risk, this document explains the value of rolling up measures of risk usually addressed at lower system and organization levels to the broader enterprise level. keywords cybersecurity risk management (csrm); cybersecurity risk measurement; cybersecurity risk. Cisa cyber essentials chapter 1: yourself, the leader video. this half hour video provides a deep dive into toolkit 1 which focuses on you as a leader and how your investment (e.g., time and money) drives actions and activities, and these build and sustain a culture of cybersecurity within your organization. A comprehensive, flexible, risk based approach the risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. the risk based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, executive orders. Cybersecurity risk management is a strategic approach to prioritizing threats. organizations implement cybersecurity risk management in order to ensure the most critical threats are handled in a timely manner. this approach helps identify, analyze, evaluate, and address threats based on the potential impact each threat poses.
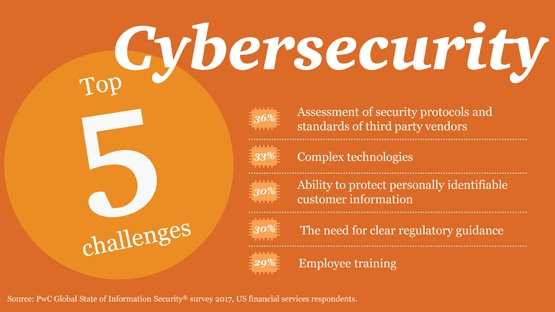
Cybersecurity Risk Management Best Practices B78 A comprehensive, flexible, risk based approach the risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. the risk based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, executive orders. Cybersecurity risk management is a strategic approach to prioritizing threats. organizations implement cybersecurity risk management in order to ensure the most critical threats are handled in a timely manner. this approach helps identify, analyze, evaluate, and address threats based on the potential impact each threat poses.

Comments are closed.