Enterprise Security Architecture For Cyber Security
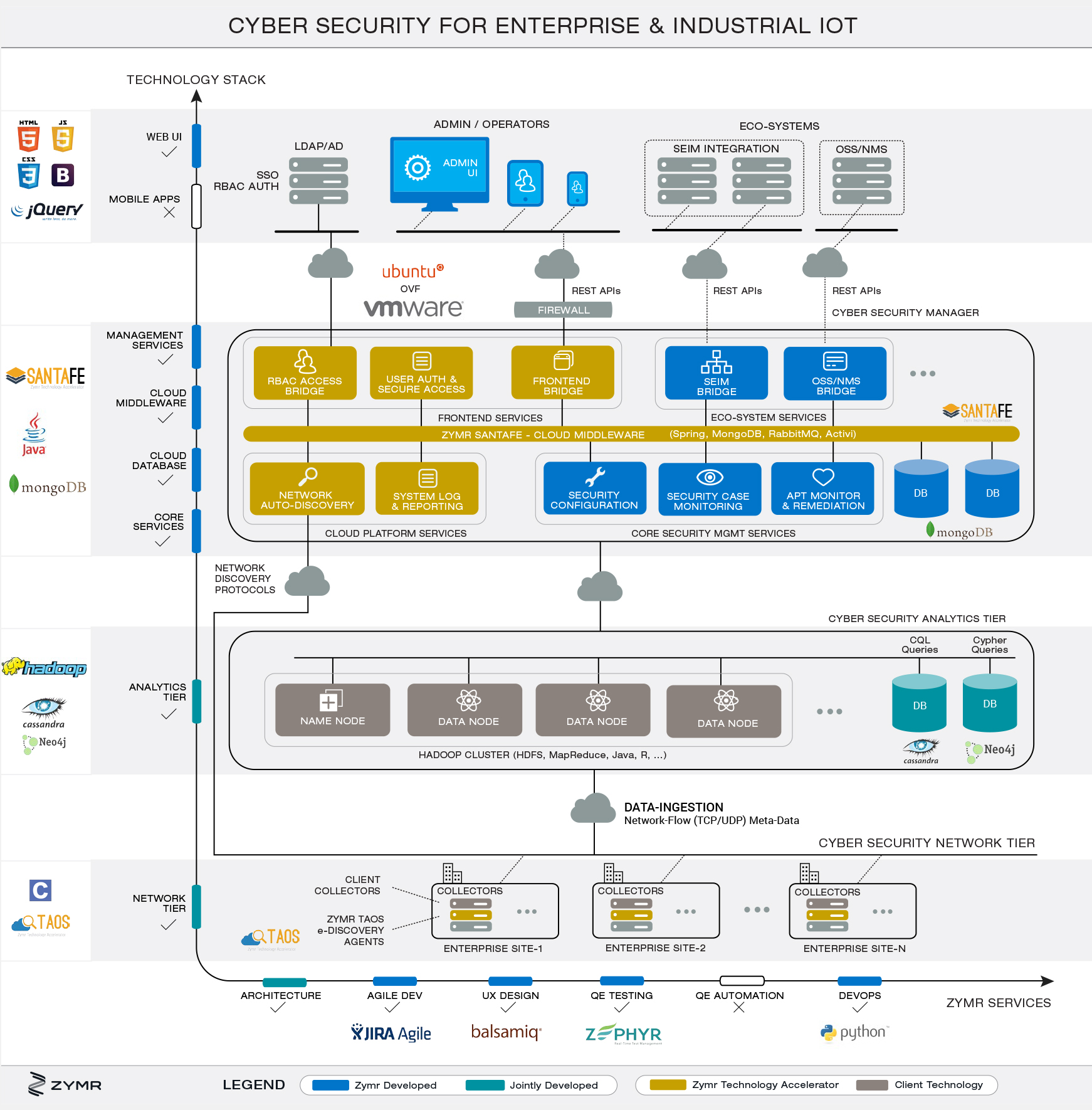
Iot Enterprise Cybersecurity Zymr If one looks at these frameworks, the process is quite clear. this must be a top down approach—start by looking at the business goals, objectives and vision. the initial steps of a simplified agile approach to initiate an enterprise security architecture program are: identify business objectives, goals and strategy. Compliance: the process for ensuring that the deployed technology conforms to the organization’s policies, procedures, and architecture. 2.3 enterprise security architecture. with the enterprise security program framework as background, the focus for the remainder of the document shifts to the o‑esa components.

Enterprise Cybersecurity Architecture Security architecture is the strategic design of systems, policies and technologies to protect it and business assets from cyberthreats. a well designed security architecture aligns cybersecurity with the unique business goals and risk management profile of the organization. security teams and hackers are often locked in an arms race. An effective enterprise security architecture is tailored to your company’s needs. it aligns security with business goals, reduces risks in a cost effective manner, and enables compliance with relevant laws and standards. continuous monitoring and improvement help ensure maximum protection of critical assets as threats evolve. 3 enterprise security architecture. a security architecture is a structure of organizational, conceptual, logical, and physical components that interact in a coherent fashion in order to achieve and maintain a state of managed risk. it is an enabler driver of secure behavior, safe behavior, resilient behavior, reliable behavior, and upholding. Secure enterprise architecture begins with an initial security assessment to identify and isolate capabilities by threat level. the assessment goes beyond identifying gaps in defense; it also involves analyzing the most critical business assets, such as proprietary trading algorithms or underwriting data that, if compromised, could result in material losses and reputational harm.

Comments are closed.