Nist Cybersecurity Framework Imindmap Mind Map Template Biggerplate

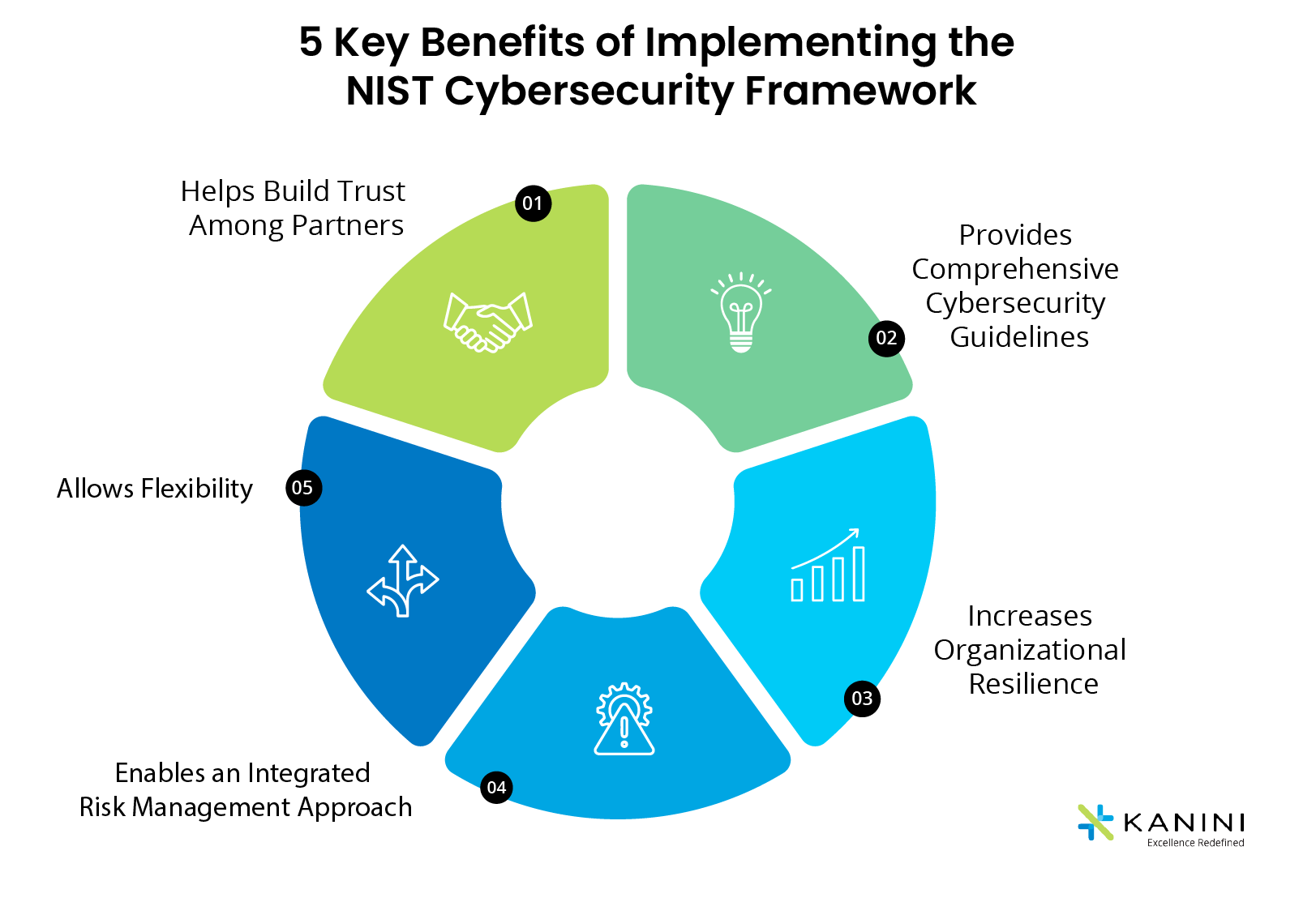
Nist Cybersecurity Framework Imindmap Mind Map Template Biggerplate Each part of the component of the framework enforces the connection between business owners and the activities of cyber security. in its composition, the framework core has five concurrent functions and continuous: identity, protect, detect, respond and recover. another free imindmap technology mind map shared on biggerplate!. The nist cybersecurity framework (csf) 2.0 provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. it offers a taxonomy of high level cybersecurity outcomes that can be used by any organization — regardless of its size, sector, or maturity — to better understand, assess, prioritize, and communicate its cybersecurity efforts.

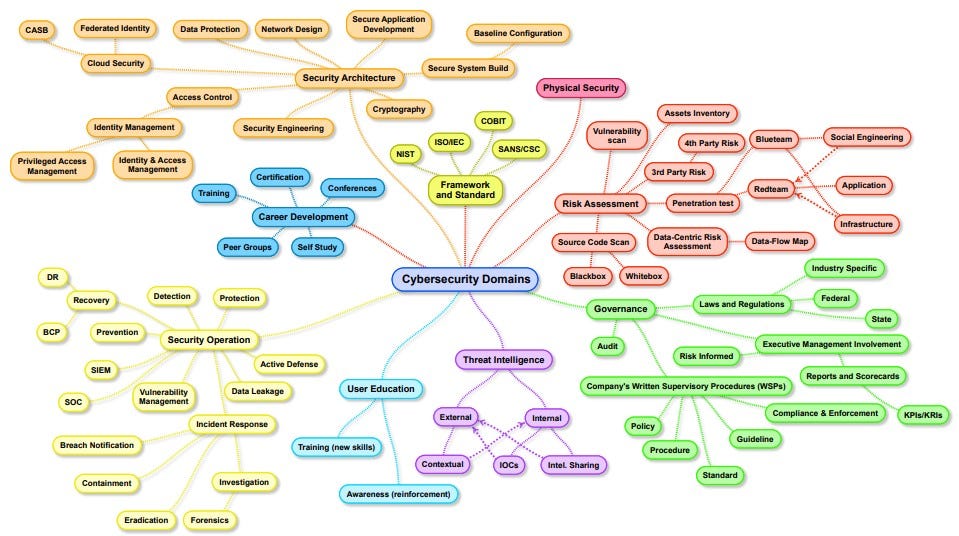
Intro To The Nist Cybersecurity Framework On march 20, 2024, nist hosted a webinar titled “overview of the nist cybersecurity framework 2.0 small business quick start guide.”. the video recording and slides are available here. aspen institute hosted a discussion on csf 2.0, including the under secretary for standards and technology and nist director laurie locascio. the video. Assessment & auditing. resources relevant to organizations with regulating or regulated aspects. (a free assessment tool that assists in identifying an organization’s cyber posture.) (a self assessment tool to help organizations better understand the effectiveness of their cybersecurity risk management efforts and identity improvement. Preface. the cybersecurity framework (csf) 2.0 is designed to help organizations of all sizes and sectors — including industry, government, academia, and nonprofit — to manage and reduce their cybersecurity risks. it is useful regardless of the maturity level and technical sophistication of an organization’s cybersecurity programs. And technology cybersecurity framework (nist csf). this guide gives the correlation between 49 of the nist csf subcatego. ies, and applicable policy and standard templates. a nist subcate. ory is represented by text, such as “id.am 5.” this represents the nist functio.
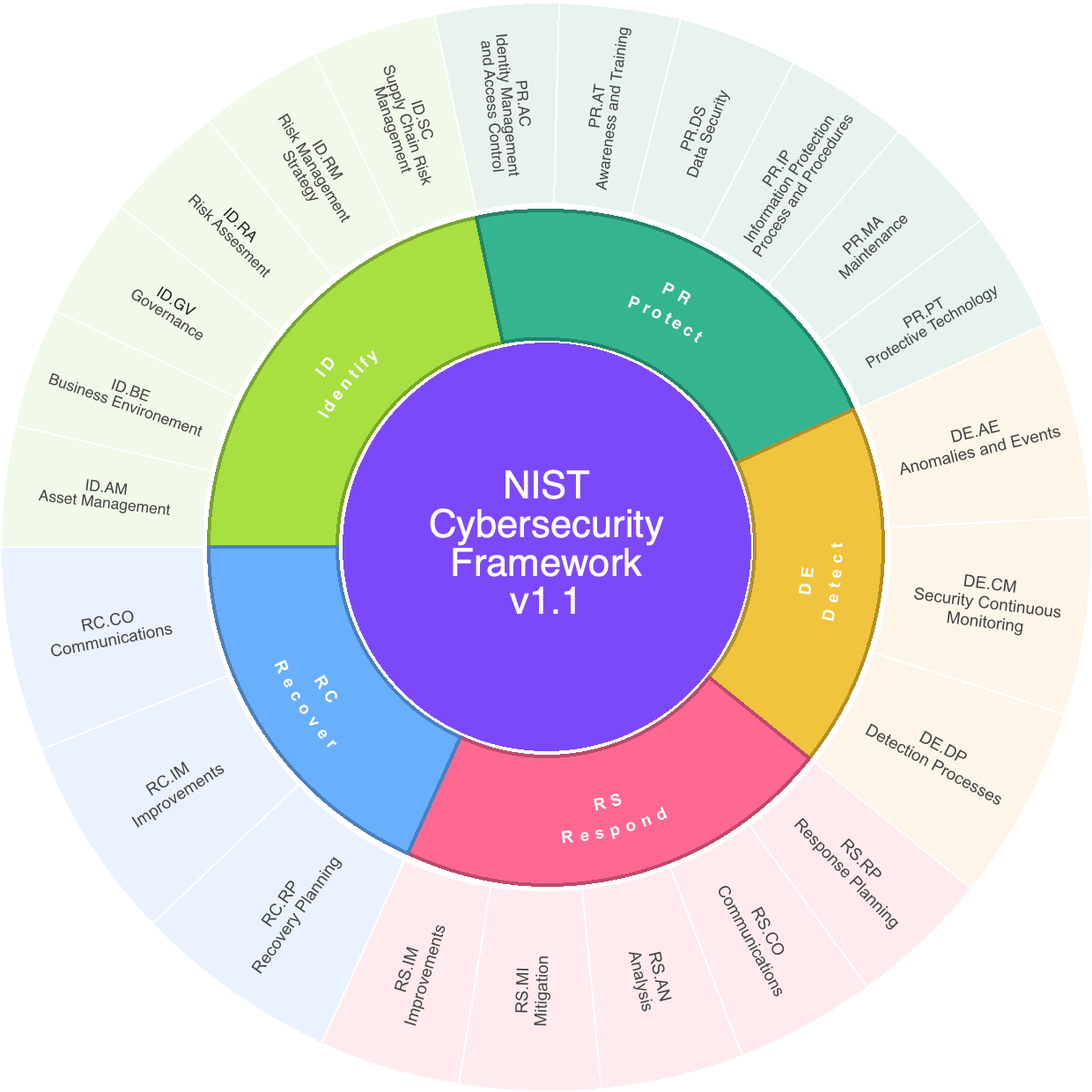
Nist Cybersecurity Framework V1 1 Mind Map Edrawmind Preface. the cybersecurity framework (csf) 2.0 is designed to help organizations of all sizes and sectors — including industry, government, academia, and nonprofit — to manage and reduce their cybersecurity risks. it is useful regardless of the maturity level and technical sophistication of an organization’s cybersecurity programs. And technology cybersecurity framework (nist csf). this guide gives the correlation between 49 of the nist csf subcatego. ies, and applicable policy and standard templates. a nist subcate. ory is represented by text, such as “id.am 5.” this represents the nist functio. The framework is organized by five key functions– identify, protect, detect, respond, recover. these five widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time. the activities listed under each function may offer a good starting point for your organization:. The new 2.0 edition is designed for all audiences, industry sectors and organization types, from the smallest schools and nonprofits to the largest agencies and corporations — regardless of their degree of cybersecurity sophistication. in response to the numerous comments received on the draft version, nist has expanded the csf’s core.
Cybersecurity The Starting Line As I Move Towards My Goals Of The framework is organized by five key functions– identify, protect, detect, respond, recover. these five widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time. the activities listed under each function may offer a good starting point for your organization:. The new 2.0 edition is designed for all audiences, industry sectors and organization types, from the smallest schools and nonprofits to the largest agencies and corporations — regardless of their degree of cybersecurity sophistication. in response to the numerous comments received on the draft version, nist has expanded the csf’s core.
Nist Cybersecurity Framework Mind Map Edrawmind 45 Off

Comments are closed.