Phishing
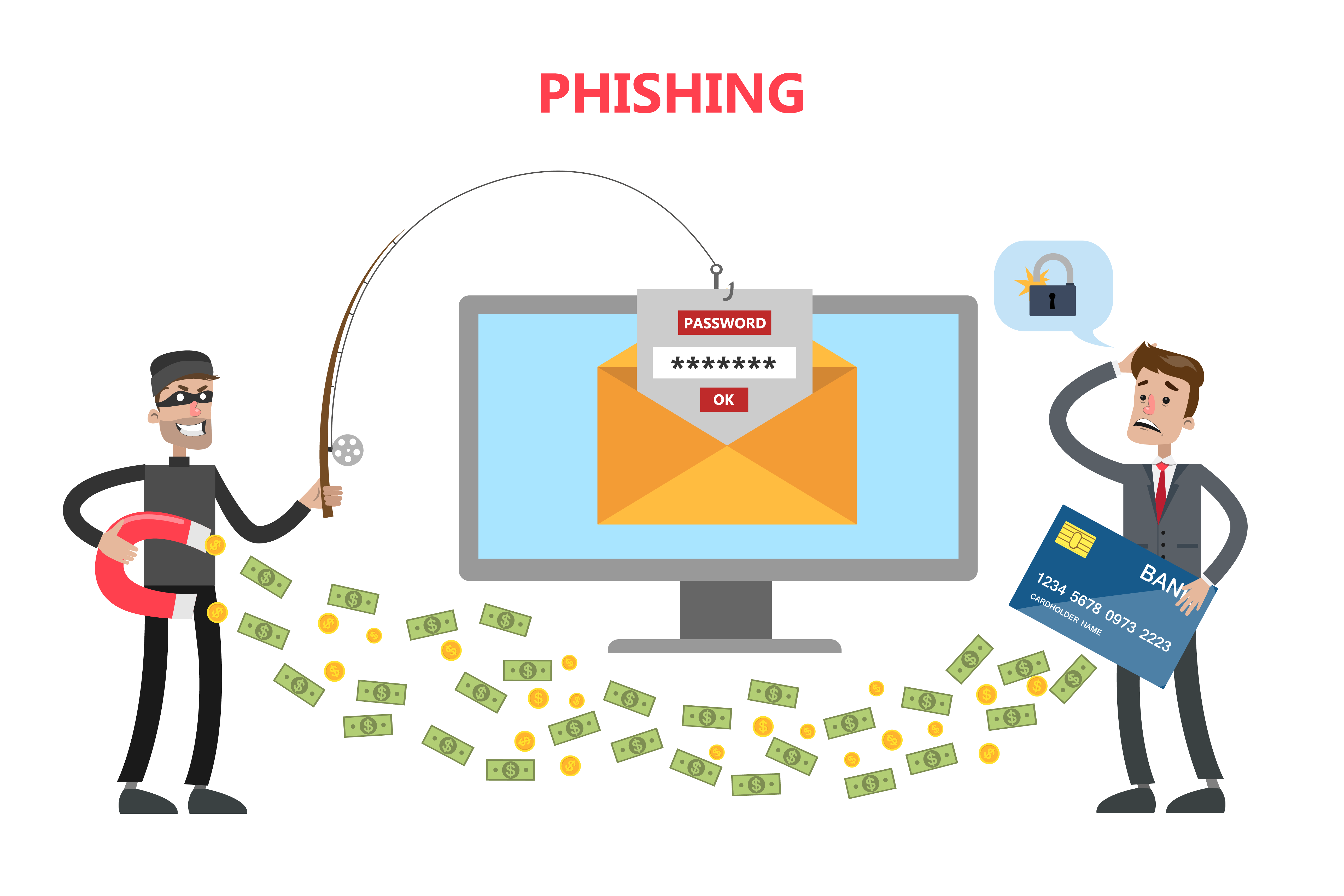
Phishing Attacks What Is Phishing Digital Defense Phishing. phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information [1] or installing malware such as viruses, worms, adware, or ransomware. phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to. Phishing is a type of cyberattack that aims to steal or damage sensitive data by deceiving people into revealing personal information. learn about the different types of phishing, common tactics, and how to protect yourself and your organization with microsoft security.

Dos Tг Rminos Phishing Y Smishing вїquг Son Y Cгіmo Evitarlos How to report phishing. if you got a phishing email or text message, report it. the information you give helps fight scammers. if you got a phishing email, forward it to the anti phishing working group at [email protected]. if you got a phishing text message, forward it to spam (7726). Phishing is a cybercrime that uses fake emails, websites, or messages to trick people into sharing personal or financial data. learn how to recognize and avoid phishing attempts, and take a free phishing security test to measure your risk. Phishing is a social engineering cyberthreat where scammers impersonate a trustworthy source and trick you into revealing sensitive data like passwords, credit card numbers, or personally identifiable information. phishing attacks often begin with scammers sending a malicious link or attachment via email, social media, or text —possibly. Sms phishing, or smishing, is a mobile device oriented phishing attack that uses text messaging to convince victims to disclose account credentials or install malware. the victim is usually asked to click on a link, call a phone number or send an email. the attacker then asks the victim to provide private data.

Comments are closed.