Protect Your Organization Against Phishing Attacks Poster Medsphere

Protect Your Organization Against Phishing Attacks Poster Medsphere Protect your organization against phishing attacks poster to reinforce your security training program, remind your staff how to avoid the dangers of online criminals who use fake emails and websites to compromise systems and steal personal information. By understanding the various forms of phishing and the tactics employed by cybercriminals, individuals and organisations can better identify and mitigate the risks posed by these insidious threats. individuals play a crucial role in mitigating the risk of phishing attacks. by adopting proactive habits and staying vigilant, they can fortify.

Cybersecurity Posters Sdn Communications Limit user access to high value systems and data. most phishing attack methods aim to exploit human operators, and privileged user accounts are attractive targets for cybercriminals. limiting. Phishing emails increase in volume every month and every year, so we created this free resource kit to help you defend against attacks. request your kit now to learn phishing mitigation strategies, what new trends and attack vectors you need to be prepared for, and our best advice on how to protect your users and your organization. here is what. Smishing: a phishing attack using sms (texts). a scammer may impersonate someone you know or pose as a service you use (e.g. internet or mobile provider) to request or offer an update or payment. quishing: a phishing attack using “quick response” (qr) codes which a scammer usually sends via email. the victim scans the qr code that re. Documentation and maintenance. finally document the complete phishing response plan, including procedures, contact information, and incident response checklists. regularly review and update the plan to reflect changes in technology, attack trends, or organizational structure. by following these steps, organizations can create a robust emergency.
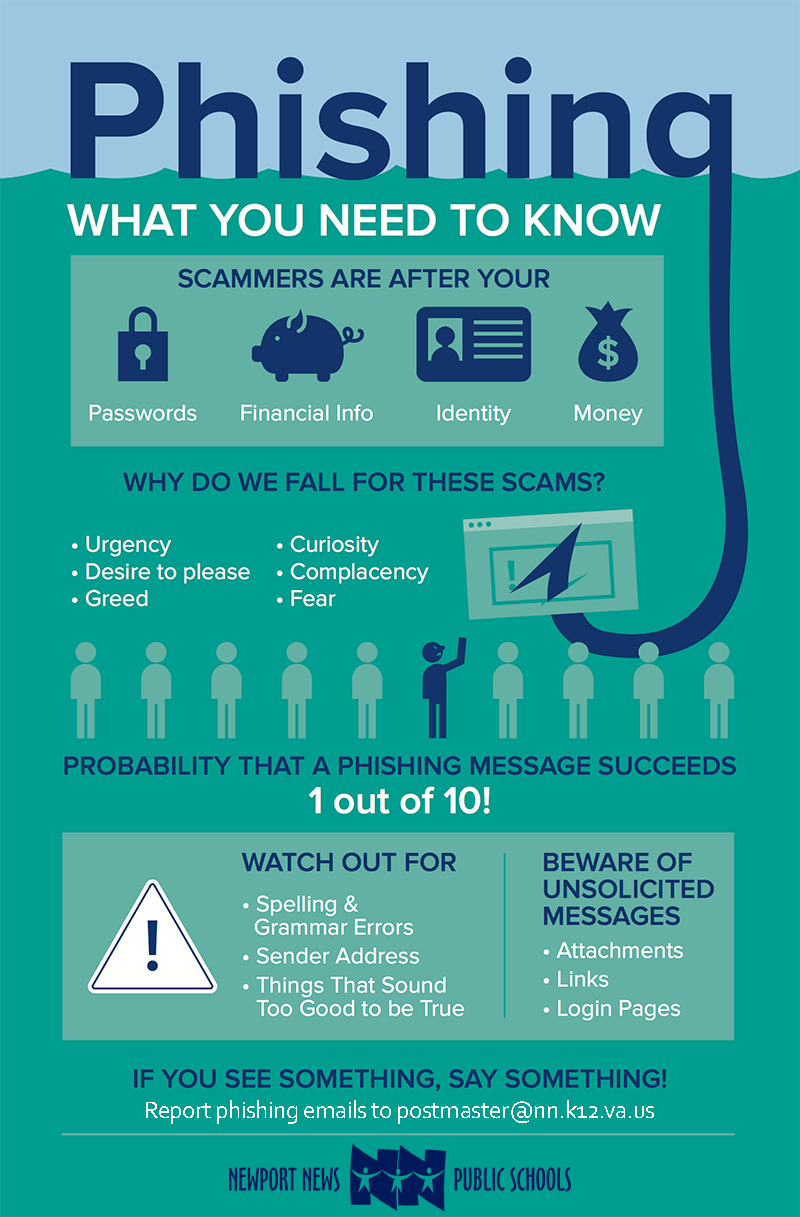
Phishing Smishing: a phishing attack using sms (texts). a scammer may impersonate someone you know or pose as a service you use (e.g. internet or mobile provider) to request or offer an update or payment. quishing: a phishing attack using “quick response” (qr) codes which a scammer usually sends via email. the victim scans the qr code that re. Documentation and maintenance. finally document the complete phishing response plan, including procedures, contact information, and incident response checklists. regularly review and update the plan to reflect changes in technology, attack trends, or organizational structure. by following these steps, organizations can create a robust emergency. Download your free phishing or cyber security poster. discover our suite of personalised security awareness training solutions, designed to empower and educate your team against modern cyber threats. from policy management to phishing simulations, our platform equips your workforce with the knowledge and skills needed to safeguard your. This way, your employees are more likely to engage in it, remember it, and apply it in an actual phishing attack. focused training yields far superior results in protecting your employees and your organization from an attack over a generalized phishing awareness training approach. 3. engage employees through action.

Protect Your Business From Phishing Attacks Cheeky Munkey Download your free phishing or cyber security poster. discover our suite of personalised security awareness training solutions, designed to empower and educate your team against modern cyber threats. from policy management to phishing simulations, our platform equips your workforce with the knowledge and skills needed to safeguard your. This way, your employees are more likely to engage in it, remember it, and apply it in an actual phishing attack. focused training yields far superior results in protecting your employees and your organization from an attack over a generalized phishing awareness training approach. 3. engage employees through action.

Comments are closed.