Risk Management Definition Strategies And Processes Pc Network

Risk Management Definition Strategies And Processes Pc Network Risk management in cybersecurity is the practice of identifying and minimizing potential risks or threats to networked systems, data, and users. following a risk management framework can help organizations better protect their assets and their business. watch overview (2:20). Free trial. it risk management is the process of managing cybersecurity risks through systems, policies, and technology. this process consists of three primary stages identification, assessment, and control to mitigate vulnerabilities threatening sensitive resources. the terms it risk and information risk are often used interchangeably.

Understanding Core Security Goals And Basic Risk Concepts Puchin The goal of it risk management, sometimes abbreviated to itrm, is to identify, assess, address, and analyze it related risks that could affect the business, improving it operations, cybersecurity, risk mitigation capabilities, and the organization’s overall risk and security posture. in general, it risk management follows the same pattern of. A risk management strategy is a strategy that addresses how an organization intends to identify, assess, respond to, and monitor risk. it may also prescribe policies, procedures, and methodologies for performing these risk assessment, risk response, and risk monitoring activities. an effective risk management strategy must consider the. Risk management framework (rmf) (rmf) provides a flexible and tailorable seven step process that integrates cybersecurity and privacy, along with supply chain risk management activities, into the system development life cycle. the nist rmf links to a suite of nist standards and guidelines to support implementation of risk management programs to. What is cyber risk management?.
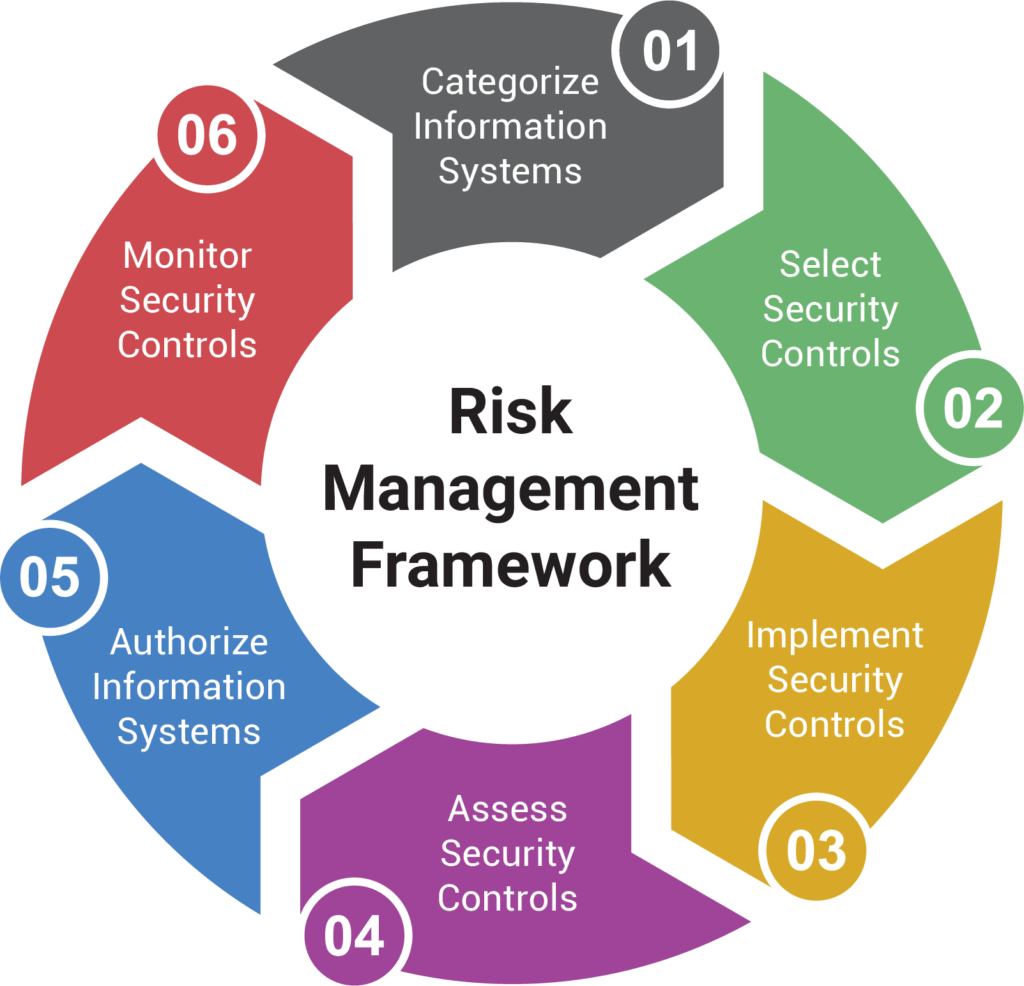
The Risk Management Framework Risk management framework (rmf) (rmf) provides a flexible and tailorable seven step process that integrates cybersecurity and privacy, along with supply chain risk management activities, into the system development life cycle. the nist rmf links to a suite of nist standards and guidelines to support implementation of risk management programs to. What is cyber risk management?. Risk management is the process of identifying, analyzing, assessing, and communicating risk and accepting, avoiding, transferring, or mitigating it to an acceptable level considering associated costs and benefits of any actions taken. effective risk management improves the quality of decision making. while risk cannot always be eliminated. A comprehensive, flexible, risk based approach the risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. the risk based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, executive orders.
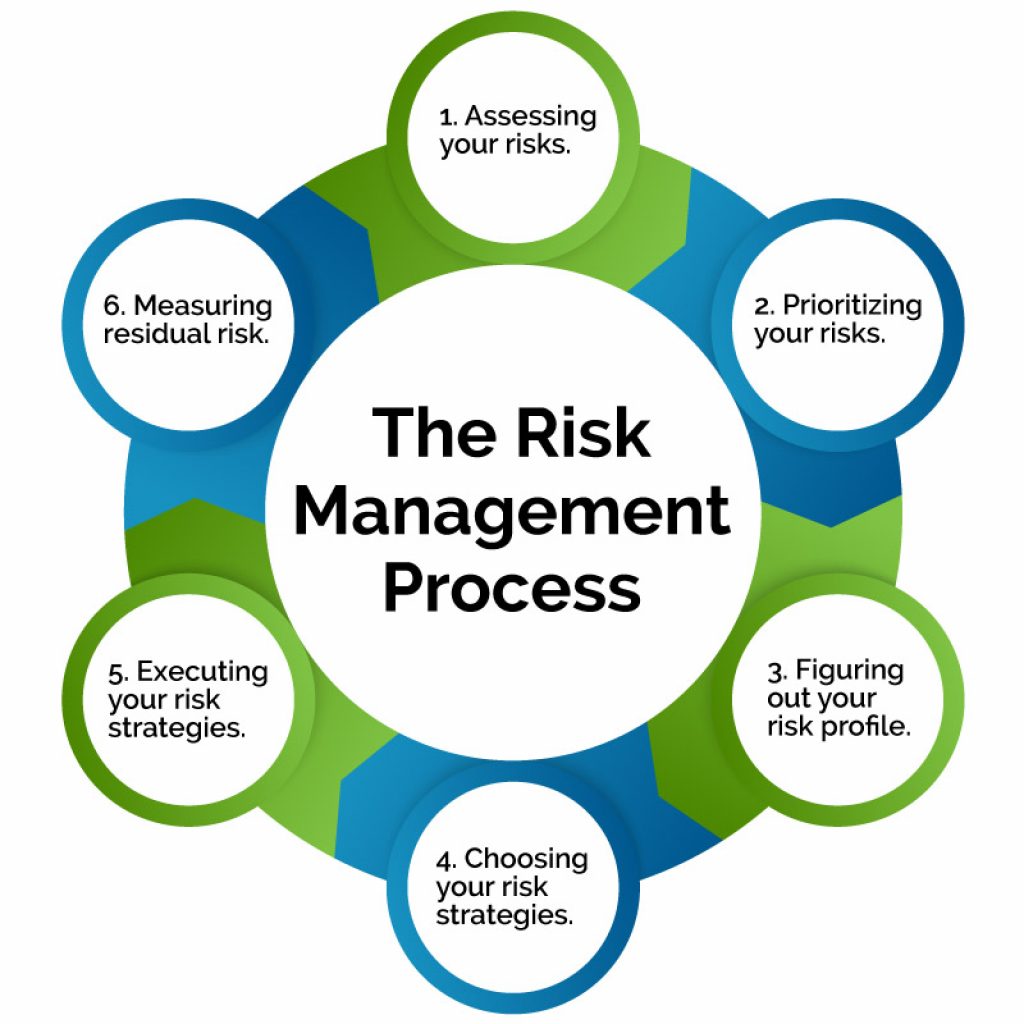
What Is Risk Management Strategy How To Have One For Your Business Risk management is the process of identifying, analyzing, assessing, and communicating risk and accepting, avoiding, transferring, or mitigating it to an acceptable level considering associated costs and benefits of any actions taken. effective risk management improves the quality of decision making. while risk cannot always be eliminated. A comprehensive, flexible, risk based approach the risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. the risk based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, executive orders.
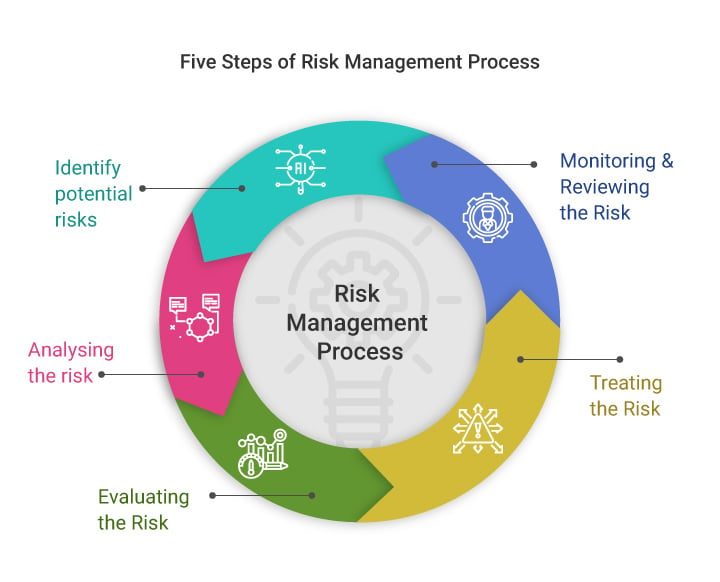
Five Core Steps Of The Risk Management Process

Comments are closed.